TCS HACKQUEST PLAYGROUND WALKTHROUGH
Hello Hackers! I hope you're doing well. This blog is a part of KeyCybr Internship.
Recently I came across the TCS Hackquest Playground, and here I'll be giving an insight into the solution for the same.
The link to register for the same is https://play.tcshackquest.com/register
This playground is like a warm-up before the actual TCS Hackquest, which is probably scheduled for January 2022.
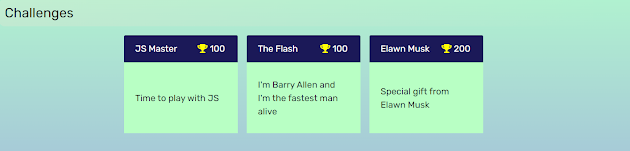
Let's dive into the challenges.
Challenge 1: Time to play with J.S.
However, to overcome this, you just need to use burpsuite or zap proxy.
Intercept request for each uuid and view the response for the same.
In one of the responses, you'll find the flag!
Challenge 3: The Elawn Musk
Download the Tweet collection CSV file.
As we analyze the file, you'll find
and you'll also see
From this line, it seems as if we have ECB. On doing further research, you'll come to know that encryption is AES 128 bit ECB mode encryption.
All you have to do is remove the first 8 bits of plain text and use the key.
After doing the same, you'll get a base 64 string. You'll bring plain text on decoding it, which you'll need to enter on the page given in the challenge.
P.S. Apologies for the blurry images😔. However, I hope that the content covered that up😄
If you like the content, consider connecting with me and pour your knowledge into my D.M.!!😇
Instagram: bhavak_29
LinkedIn: https://www.linkedin.com/in/bhavak-kotak-3b6b071b1/
"Images belong to their respective owners."












Comments
Post a Comment