Helping Rick find his ingredients: PICKLE RICK CTF
Hello Hackers,
Today we are going to solve the challenge PICKLE RICK by TRYHACKME.
So the story goes like this:
Our friend Rick has turned into Pickle [Really don't know how he ended up being a Pickle :P] and our goal is to find him 3 Secret ingredients so that he can go back to his original form.
Let's jump into the CTF.
First things first
CONNECT TO OPENVPN & DEPLOY THE MACHINE😂
We'll see this page as we put the IP address into our browser.
REMEMBER: Whenever you visit a webpage, don't forget to check the source code. Sometimes, developers leave sensitive information such as credentials in the form of comments.
You can either do Right-Click --> View page source or press Ctrl+u.
You'll see that the username is leaked in the source code of that page!
Now let's try to scan the ports and see if we find something interesting.
Command used: nmap -sV -A -T5 {ip}
You'll see that ports 22 & 80 are open.
Wait, can the username be for the ssh service?
Let's try it out.
Type ssh {username}@{ip}
You'll see that actually, it was not for ssh.
No worries, let's try to carry out directory brute force.
As you can see, that's surely not a normal robots.txt file because generally, it contains instructions for the pages that web crawlers are not allowed to crawl. This leads us to think that it might be the password!
Well, we know what to do now. Looking in other directories!
Command used: pwd
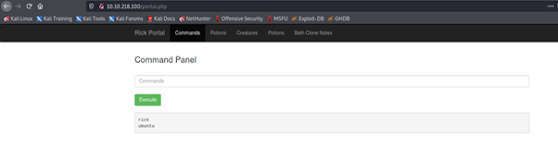
Command used: cd ../../../ ; cd /home ; ls
You'll see two directories. Rick and Ubuntu.
Let's see what's inside the Rick directory.
Command used: cd ../../../ ; cd /home/rick ; ls
That's the file containing the second ingredient!
Unfortunately, the cat command is blocked :(
Don't worry just take the help of your friend GOOGLE.
We can make use of less command to fulfill our purpose.
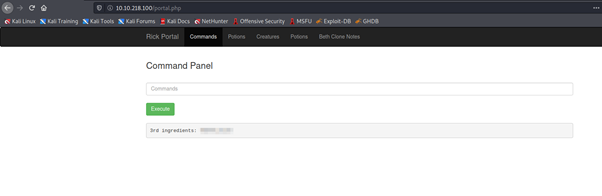
Command used: cd ../../../ ; cd /home ; cd rick; less "second ingredients"
And there you have it! The second ingredient!
Let's hunt down the last ingredients as well. For this, you'll have to visit the root directory.
Type cd ../../../; ls /root
And that's it!
Congratulations! We've found all the three ingredients🎉
I hope Rick gets back to his original form soon. Until then cya!
Key Takeaways:
- Have a habit of looking at the source code of the web pages.
- Never miss out on making educated guesses.
- Look for alternate commands if a particular command is blocked.
P.S Apologies for the blurry images😔. However, I hope that the content covered that up😄
If you like the content then do consider connecting with me and pour your knowledge into my DM!!😇
Instagram: bhavak_29
LinkedIn: https://www.linkedin.com/in/bhavak-kotak-3b6b071b1/
DO NOT FORGET TO CHECK OUT TRYHACKME FOR MORE INTERESTING ROOMS.




















Comments
Post a Comment